
DORA: how to move from operational risk management to operational resilience?
DORA: how to move from operational risk management to operational resilience?
Wed 25 Oct 2023
DORA (the Digital Operational Resilience Act) is the key regulatory outlook for IT and Cyber risk between now and 2025. The European Supervisory Agencies have sought to strengthen the resilience of institutions by emphasising the need to evolve the approach to operational risk management, of which information and communication technology risks are a part. DORA strengthens the digital side of the financial sector’s operational resilience through network security measures.
This comes amid the directive and the DORA regulation being drawn up to meet three key challenges:
- This dependence is likely to increase with the use of technologies such as blockchain and artificial intelligence.
- Identified shortcomings in operational resilience, including a lack of involvement on the part of management bodies.
- Disparities within the EU and lack of a single legal act.
DORA should be considered a lever for harmonising national and European texts that prioritises simplification and rationalisation.
DORA scope of application
DORA applies to all players in the financial sector: asset management companies, investment firms, credit and payment institutions, account aggregators, insurance and reinsurance companies, and crypto asset service providers, according to MiCA (Markets in Crypto-Assets). It should be noted that central counterparties, trade repositories, and rating agencies will also be included in the scope of DORA. This scope will be extended beyond the financial sector, as DORA promotes the first EU-wide supervisory framework to identify and supervise critical IT service providers. These requirements will be applied proportionally according to the size and nature of the company’s activities.
DORA implementation times
The DORA regulation came into force in January 2023 and will be applicable from January 2025 by all EU member states. It aims to establish a detailed and comprehensive digital operational resilience framework for EU financial institutions. Although the text has been finalised, many are yet to be published. These include those that detail more operational and technical aspects which specify:
- Elements to be included in IT security policies, procedures, protocols, and tools;
- IT controls to be integrated into systems right from the design stage (security by design);
- Incident evaluation criteria;
- How to carry out certain intrusion tests.
The diagram below shows the various key dates in the implementation of DORA:
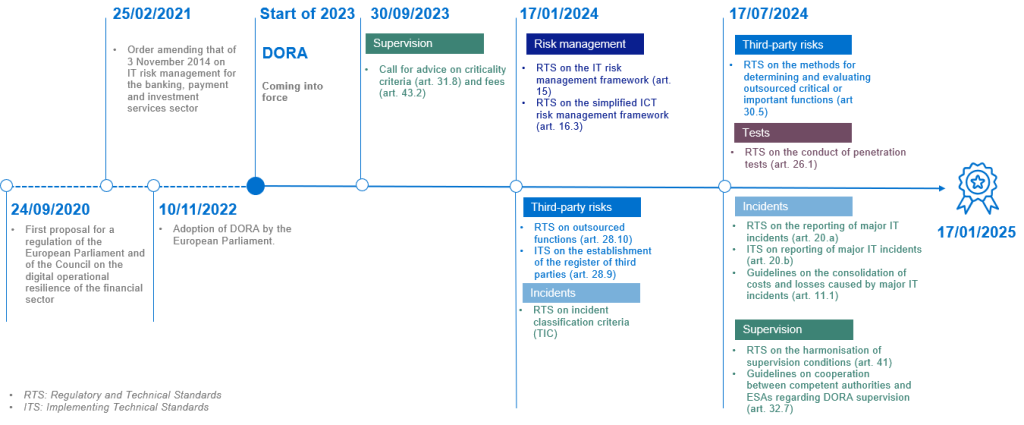
The five pillars of DORA
DORA identifies and proposes requirements for five key pillars of digital operational resilience that financial institutions must consider:
- Strengthening the IT risk management framework
- IT incident reporting
- Information sharing
- Digital operational resilience testing
- Third-party risk management
Strengthening the IT risk management framework
DORA aims to strengthen the IT risk management framework, promoting a holistic view of IT and security risks within financial institutions. This is the backbone of DORA which lays down the fundamental principle of full responsibility, for the aim is to ensure that management and supervisory bodies are involved in the management of IT-related risks. This has been translated into specific requirements:
- Appropriate level of tolerance to IT-related risks;
- IT business continuity policy;
- Disaster recovery plan;
- Investment in IT;
- Training for members of the management body;
- Formalised digital operational resilience strategy.
It also reaffirms the principle of the three lines of defence within which the pillars of operational resilience must be developed. DORA reinforces existing governance and risk management rules but requires breaking down silos to foster digital operational resilience. The management body must have IT and cyber risk expertise. These requirements will facilitate improving the human capital of financial entities by setting up a training program for members of management bodies and awareness-raising initiatives.
IT incident notification
DORA harmonises the management of IT incidents, particularly those with the greatest impact, by defining a framework structured around four main stages:
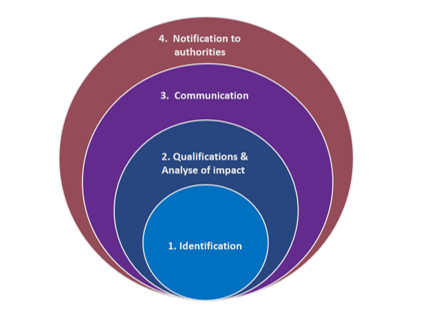
The first two stages are generally in place, in line with ITIL (the Information Technology Infrastructure Library) or COBIT (Control Objectives for Information and Related Technologies) best practices. DORA sets out the main areas of analysis for qualification:
- The number of users or financial counterparties affected;
- The duration of the incident, including service interruption;
- Geographical distribution and areas affected, particularly if more than two Member States are involved;
- Loss of data, such as loss of integrity, confidentiality, or availability;
- The severity of the incident’s effects and the criticality of the services affected;
- Economic consequences, in absolute and relative terms.
Notification to the authorities concerns only major incidents for which a harmonised nomenclature will be published in the RTS. A dedicated file will be formalised according to a strict timetable (one day, one week, and one month after the incident). The asset management sector has not been spared the risk of cyber-attacks.
In fact, the AMF (French Financial Market Authority) has recorded some twenty incidents since 2020 (Société du Grand Paris scope), with recurring attack patterns such as misappropriation of individual authenticators, impersonation of corporate bodies or individuals, disclosure of specific professional or personal information, or intrusion into the information system.
Information sharing
Article 40 provides for the possibility of sharing information on defence systems and threats between financial entities, on a voluntary basis.
Considering the potentially sensitive nature of the information shared, exchanges are governed by rules of conduct that fully respect business confidentiality, personal data protection, and competition policy guidelines. Here, the regulator emphasises the importance of organising and sharing information between players to strengthen the sector’s overall resilience.
Digital operational resilience testing
DORA brings together the major resilience principles set out in the latest European and sector-specific texts and is thus positioned as an ‘umbrella’ text. It is not an overlay, but rather a consolidation of systems that meet different requirements. DORA offers a holistic vision of the risks, or threats, that can affect resilience, whether they be IT, cyber or physical. This requires the definition of a global resolution strategy of tests according to the different threat scenarios defined by the entity. A robust and comprehensive program of digital operational resilience testing must be developed and conducted. The principle of proportionality applies to the requirements for conducting resilience tests according to the size, activity, and risk profile of entities.
Third-party risk management
DORA lays down the principles for managing the relationship with the service providers throughout the life of the contract from conclusion, execution, termination, and post-contract, in line with the EBA’s (European Banking Authority) guidelines on outsourcing. It also provides for the creation of an EU-wide supervisory framework to identify critical service providers. Each service provider will be supervised by a supervisory authority. This authority will be able to sanction service providers, notably through financial penalties.
Authorities will have to annually draw up, update, and publish a list of critical IT service providers in the EU, with cloud providers receiving special attention from the regulator.
Points of attention for ManCos
Cyber SPOT checks carried out at management compagnies (ManCos) in 2019 and 2020 revealed several weaknesses:
- Failure to identify critical assets in advance, leading to a false sense of security;
- Tested business continuity plan but omitted data restoration component;
- Inadequate management and control of critical IT suppliers;
- Persistent security flaws (no locking of USB peripherals, unencrypted workstations).
The summary of the AMF’s SPOT controls also shows that the growing sophistication of the attacks reflects hackers’ perfect mastery of data exchange flows between ManCos and their external service providers. DORA should help strengthen IT risk management and operational resilience.
How to prepare for DORA
Many elements remain to be specified in the next RTS and ITS. However, work should start immediately to diagnose the existing situation and assess the workload and the IT, human process, and training impacts required to spread a genuine culture of operational resilience. As such, we believe that projects should be managed in four key stages:
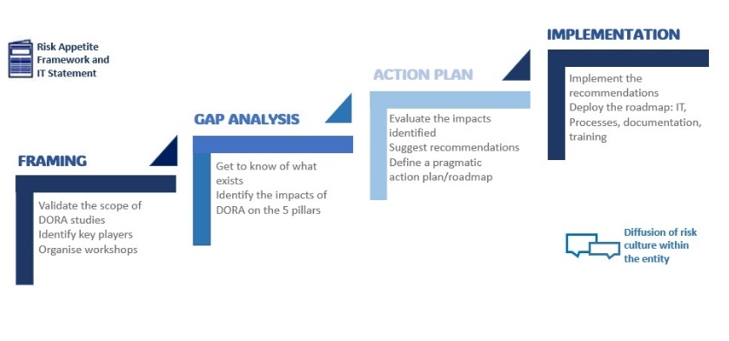
DORA will come into force at the beginning of 2025. The work initiated by certain banks and insurance companies shows that the text covers numerous cross-functional themes and represents a significant workload. The key factors for its success include:
- Raising awareness and obtain the support of the Group’s or entity’s top management;
- Defining a global resilience strategy;
- Develop and disseminate an IT risk culture;
- Integrating IT risk into the company’s Risk Appetite Framework;
- Having a holistic view of current and forthcoming regulations, thanks to the implementation of a regulatory watch.
Want to get notified when new blog posts are published?
Subscribe

Our top risks for financial services firms in 2024
We have identified and ranked the key risks for financial services business leaders in 2024 based on market research, regulatory insights as well as our assessment of the current difficulties facing firms. We also highlight the changes in risk rankings compared to last year, justified by global events and new regulations that have surfaced in […]

The insurance industry in flux: what changes are currently unfolding?
The regulatory requirements for insurance companies are becoming increasingly complex. In this interview, Marc Böhlhoff and Thomas Volkmer, Partners at Mazars in Germany, discuss the impact of this change on the industry and delve into what it means for the operations of auditing and consulting firms. Mr. Volkmer, the insurance industry is undergoing rapid change. What […]

Being an Independent Non-Executive Director in different jurisdictions: lessons learned from Mazars in Ireland roundtable
Mazars recently hosted a Financial Services INED Roundtable Dining Event in Dublin[1]. Over 50 financial services independent non-executive directors (INEDs) attended, from banking, asset management, funds and insurance entities operating across the EU and UK. The roundtable focussed on the challenges facing INEDs in the current unpredictable macroeconomic environment. The new and emerging risks and […]

The European Central Bank’s priorities for 2024: where do we stand after the first quarter?
The European Central Bank (ECB) issued the SSM supervisory priorities for the 2024-2026 cycle on 19 December 2023. They sum up what institutions under the direct supervision of the ECB should expect in terms of areas of supervision, in 2024 notably, and allow firms to prepare themselves for forthcoming onsite inspections or thematic reviews. Please […]

EUROFI financial forum: strengthening economic union and European competitiveness
The Eurofi financial forum is a setting for exchanges between European Union (EU) economic and financial regulators and senior financial sector executives from the industry. It occurs bi-annually alongside the Economic and Financial Affairs Council configuration (ECOFIN) meetings. This summary takes stock of the Eurofi discussions, as well as recent publications by the EU Commission […]

Drafting the future: unveiling the next chapter of DORA
DORA is a legislative proposal that aims to improve the digital operational resilience and ensure the performance and stability of the financial system of the member countries of the European Union in the face of the risks associated with ICT (Information and Communication Technology) in the financial sector (cyber-threats, cyber-attacks). The DORA requirements will apply […]

IIF annual membership meeting: building resilience amid turbulence and transformation
The IIF Annual Membership meeting is a setting for insights and perspectives from global financial regulators and senior financial sector executives on topical economic and regulatory issues. Being a forum with global coverage means that it is a valuable setting for picking up future economic and regulatory directions. A packed agenda under the theme of Building […]

Market in crypto assets regulation: where we stand now
On 29 June 2023, the European Union’s (EU) Markets in Crypto Assets Regulation (MiCA) entered into force. It is being implemented in stages depending on the provisions, between June and December 2024. The regulation, which provides clearer rules for crypto-asset service providers and token issuers, is much needed for this fast-changing industry. The rapidly approaching […]

New DORA regulation: the challenge for insurers to strengthen their IT and cyber risk management
Since the onset of 2023, regulatory news has been adorned with the latest European legislation, under the acronym DORA, adopted on 10 November 2022 by the European Parliament. Standing for the Digital Operational Resilience Act, it will apply to the members of the European Union from 2025, and concerns companies in the financial sector specifically. […]

The European Parliament devises a new agreement to restrict access and abuse of financial services information
New measures to combat money laundering and terrorist financing The European Parliament has adopted a set of stringent measures to strengthen the fight against money laundering and terror financing, alongside circumventing sanctions within EU. These regulations are presented by EU in the form of a “legislative package” comprising three key measures which provide various practical […]

Equipping NEDs to challenge private investment valuations
A recent major board reshuffle in one of Europe’s largest listed investment companies has focused attention on private investment valuations. It follows concerns raised by an ex-director over the robustness of the directors’ processes for approving investment valuations. The issues primarily question whether the Board of Directors has sufficient training and experience and whether governance […]

The use of post-model adjustments to capture emerging risks
Since the Covid-19 pandemic, post-model adjustments1, or management overlays, have become an increasingly common and accepted mechanism used by banks to manage expected credit losses (ECLs). The number of post-Covid unprecedented events related to the war in Ukraine, energy crisis and global economic uncertainty has raised a number of questions relating to the consistency and […]

Lessons from the spring 2023 banking turmoil: five areas for banks to focus their attention
The Basel Committee on Banking Supervision (BCBS) and Financial Stability Board (FSB) published reports in October 2023 on the causes and lessons learnt from the Spring 2023 banking turmoil. The BCBS report provides an assessment of the causes of the banking turmoil, the regulatory and supervisory responses, and the initial lessons learnt. The FSB report […]

Managing tomorrow’s banking risks
While the banking sector has shown resilience over recent years, the economic environment and geopolitical situation remain tense. So, what does this mean for risks to the banking sector? More specifically, what is the impact on capital requirements for banks with the implementation of the Capital Requirements Regulation (CRR3) and the Capital Requirements Directive (CRD6), […]

Our top risks for financial services firms in 2024
We have identified and ranked the key risks for financial services business leaders in 2024 based on market research, regulatory insights as well as our assessment of the current difficulties facing firms. We discuss in this article the key takeaways for you and your organisation. A more detailed assessment can be found here, which contains […]

Adapting governance to spearhead sustainability more effectively
There are increasing regulatory expectations globally for financial institutions to disclose and demonstrate how sustainability-related responsibilities are allocated within the organisation. In this respect, the increasing global trend towards mandatory sustainability disclosure frameworks continues to underscore the significant role that the finance function is anticipated to assume in sustainability. It’s a trend reflected in Mazars’ […]

SRB annual conference 2024: entering a new phase of banks testing and operationalisation of resolution plans
The Single Resolution Board (SRB) convened its annual conference on 13 February 2024 with a theme highlighting the focus for the year: ‘The road ahead: risk, readiness and resilience’. While significant strides have been made with the EU banking resolution framework and tools, the SRB’s Chair Dominique Laboureix recalled this is not the end of […]

Unveiling the European Central Bank’s strategy: data, scenarios and models
In January 2024, the European Central Bank (ECB) published its Climate and Nature Plan for 2024-2025. This plan aims to: This plan underscores those financial risks stemming from climate change remain a key area of attention for the ECB. The ECB will continue working on several topics including stress testing, scenarios and climate-related data, and […]

Assessing materiality and verification of sustainability disclosures
In environmental, social and governance (ESG) reporting, materiality is crucial for enhancing transparency and accountability in sustainability and climate-related disclosures. Importantly, it helps identify and report on matters that are deemed significant, emphasizing their relevance to stakeholders. Materiality comes in various forms. Financial materiality focuses on sustainability issues impacting financial performance, aligning with annual financial […]

How banks and insurers have progressed in embedding sustainability into their businesses
In late 2023, and to coincide with COP 28, Mazars published its latest Sustainability practices survey on the progress banks and insurers have made in embedding sustainability into their businesses, our most comprehensive and information-rich report to date covering 404 executives in banks and insurance companies in 16 countries Despite sustainability being in the limelight […]

IBOR transition: impacts of the SOFR discounting switch
An important milestone in the IBOR transition is the change in rates used by LCH and CME for discounting and Price Alignment Interest (PAI) calculations for USD OTC cleared swaps. Indeed, on October 16, 2020, they moved from using the daily Effective Federal Funds Rate (Fed Funds) to the Secured Overnight Funding Rate (SOFR) for […]

IBOR Transition: Modelling RFR term rates to price IR derivatives
One of the anticipated challenges in the transition from IBOR rates to risk-free rates (RFRs) is the management of its impact on quantitative models. The ones currently used for pricing IBOR-linked financial instruments account for term rates which are “forward-looking”. The RFRs replacing the IBORs are all overnight rates. This means that a term rate […]

TRIM: Is Winter Coming for Internal Models?
Measuring banking risks is a difficult exercise, but striking a balance between simplistic and overly complex measurement techniques is the key to accurate risk measurement. This was the substance of the European Central Bank’s (ECB) Chair of the Supervisory Board, Danièle Nouy, in a speech at the Austrian Chamber of Commerce in Vienna, on 2nd […]

Data privacy – too strategic for boards to ignore
Personal data security is increasingly important, but many companies may not be ready to comply with the EU’s tough new data protection laws, which must be implemented by May 2018. All EU businesses that handle data will have to comply with the General Data Protection Regulation (GDPR), which will require investment in systems and training […]

Evolving role of AI with cyber risk
Cyber as an organsational risk In 93% of data breaches, the targeted systems were compromised within minutes. 83% of the time, those breaches were not discovered for weeks, leaving the attackers with plenty of time to do their damage and exfiltrate data[1]. The average consolidated total cost of a U.S. data breach in 2016 was […]

The Reduction of Regulatory Compliance Examinations for Financial Institutions
Examination Cycle for Certain Small Insured Depository Institutions and U.S. Branches and Agencies of Foreign Banks Under $1 Billion in Total Assets. The Federal Deposit Insurance Corporation (“FDIC”), the Federal Reserve Board (“FRB”), and the Office of the Comptroller of the Currency (“OCC”) issued joint final rules that increased the number of small banks and […]

EBA opinion on IFRS 9 and the impact on regulatory capital
After the Basel Committee consultation in October and then the European Commission’s legislative proposal of the package CRR II / CRD V in November 2016, the EBA has now given its opinion on the management impact of IFRS 9 on regulatory capital, notwithstanding a second impact study has just been completed. This opinion, primarily addressed […]

Creating a compliance pathway for dealing with NPLs
Non-Performing Loans (NPLs) are a key issue and will continue to be on the European agenda as a top priority for a long time. On the one hand, the ECB guidelines are already applicable, as they represent a best practice reference for the day-by-day work of the Joint Supervisory Teams. On the other hand, the […]
An IBOR revolution is on its way
The whole financial system relies on reference interest rates, more precisely on InterBank Offered Rates (IBORs) whose integrity and reliability have raised some concerns since the 2008 financial crisis and the LIBOR manipulation scandal. These IBORs are used to determine the unsecured short-term funding cost in the interbank market for a combination of currencies, tenors […]

Key takeaways & industry challenges following the ECB TRIM project – a focus on CCR (Part 1)
Click here to read ‘Key takeaways & industry challenges following the ECB TRIM project – a focus on credit risk (Part 2)’ As articulated by the ECB in its recent TRIM reporting, the 236 findings cover different key aspects of supervised entities Internal Model Method (IMM) models & frameworks. Remediation actions are underway in all […]

Key takeaways & industry challenges following the ECB TRIM project – a focus on credit risk (Part 2)
The Targeted Review of Internal Models (TRIM) was one of the largest projects by the European Central Bank (ECB) aimed at identifying potential sources of unwarranted or non-risk based variability in Significant Institutions (SIs) risk-weighted assets (RWA) from the use of Pillar 1 internal models such as Probability of Default (PD), Loss Given Default (LGD) […]

What’s at stake with the ECB draft guidance to banks on non-performing loans?
The European Central Bank (“ECB”) recently launched public consultation on guidance to banks on non-performing loans (“NPL”). Consultation periods runs until 15 of November 2016. As NPL harms the profitability, funding and capital of banks and more globally the real economy, the ECB issued this guidance, aiming to achieve common practices for how to handle […]

2021: The year of Brexit for banks
Brexit, or the UK’s departure from the European Union, became a reality on 1 January 2021. In terms of the regulatory impact for the financial sector, and the banking sector in particular, the UK being a third country, UK banks can no longer benefit from the European passport for their continental activities. Therefore, they can […]

The management of regulatory capital following the transition to IFRS 9
On 1 January 2018, banks applying IFRSs move into a new era with the implementation of IFRS 9 on financial instruments, which will supersede the existing IAS 39. Although adopting this new standard will lead to many changes, it was phase 2 of the standard, on provisions, that interested the Basel Committee on 11 October, […]

Remote working: A growing target for hackers
The widespread use of working from home (WFH) during the pandemic, regardless of sector or geographical location has required organisations and their information systems (IS) management to be very agile in deploying or increasing their capacity for remote collaboration. Some institutions were already prepared – for example, following the wave of strikes at the end […]

Sustainable banks must manage their risks
At a time when the European Banking Authority’s stress tests have provided valuable insights into the solvency levels of European banks, these banks are continuing their efforts to formalise the conceptual and operational framework of risk management. While changes in capital requirements (the Basel Pillar 1 quantitative requirements) still command the attention of bankers and […]

GDPR has controls over subcontractors in its line of fire
Like all industries, the real estate sector has to implement a range of legal, technical and organisational measures to protect the personal data of its employees, customers, prospects and suppliers. Processing must comply with several regulations related to data protection, including, for example, the General Data Protection Regulation (GDPR), applicable since 25 May 2018. Same […]
IBOR transition and FRTB cross dependencies highlighted
The revised market risk framework – also known as the Fundamental Review of the Trading Book (‘FRTB’) – not only impacts an institution’s regulatory capital charge calculation for market risk, but also affects operational, governance and business strategies. FRTB brings significant change. With the aim of harmonising capital standards for market risks across jurisdictions and […]

Covid-19 US policy changes: what banks need to know
Impacts from the COVID-19 pandemic have reverberated across every part of the global economy. Small businesses are struggling to pay their employees, banks are grappling with collapsing local economies, and many borrowers across the nation cannot meet their monthly mortgage payments. Banks will play a critical role in supporting their communities through this crisis, and […]
IBOR Transition: modelling of SOFR risk factors
One of the major challenges of IBOR transition is the availability of historical data on alternative risk-free rates (RFRs) required to implement interest rate model changes or re-calibration. With the Secured Overnight Financing Rate (SOFR) only published since April 2018, the available time series do not provide enough observations for risk modelling. Adding to that, […]

Is Asia on its way to IBOR transition?
With Libor’s cessation date at the end of 2021 looming, global regulators are hastening their IBOR fallback strategies. Yet while market momentum has increased for multiple published RFR indices, among them the GBP SONIA, the EUR €STR, and the USD SOFR, Asian economies, some of which rank among the world’s largest, continue to lag. While […]

Digital transformation and integration with Enterprise Risk Management
Digital transformation has expanded the need for security, continuity and resilience. Today’s business must embrace an enterprise risk management strategy that includes legal, regulatory and political considerations. Enterprises today face a significant level of security challenges across their organizations. IT is no longer a secondary priority; it is now at the very heart of the […]

IBOR Reform – key takeaways
With significant IBOR reform on the horizon, Mazars brought together industry experts, practitioners and regulators to discuss the challenges and opportunities they face. Speakers included the Bank of England Market Division’s Alastair Hughes, EFRAG’s Didier Andries and Mazars’ IBOR lead, Pauline Pelissier. From a comprehensive and illuminating session, Pauline sums up the key takeaways: “What […]

New regulatory requirements for insurance companies – focus on Germany
Because of its importance in society, the insurance industry has always faced a considerable amount of regulatory requirements at the national (BaFin) and international (EIOPA) level. Although this is generally something to be welcomed, this also presents a range of different challenges – not least because the regulations have indirect effects and unintended side effects. […]

LIBOR reform: Setting the cat among the pigeons
Could the transition period towards the new alternative Risk-Free Rates (RFRs) be more complex than initially envisaged? The speech given by Edwin Schooling Latter, Director of Markets and Wholesale Policy at the Financial Conduct Authority (FCA), on the 28 January 2019, suggests this might be the case. While Mr Latter re-affirmed that the key focus […]

The Basel Committee finalises the Basel III agreements
On 7 December, after several years of negotiations (starting in 2012 with the market risk review), Mario Draghi, chair of the Basel Committee’s Group of Governors and Head of Supervision (G-HOS), announced the finalisation of the Basel III agreements. These represent the final stage in the post-financial crisis reforms to the prudential regulations. For the […]

Conduct Risk should not be underestimated during IBOR Transition
With little more than two years to go, Libor’s cessation date continues to near. The voluntary agreement of panel banks submitting to Libor will conclude at the end of 2021, from which risk-free rates (RFR) are expected to replace Libor and similar indices. Are corporates paying enough attention to Libor updates? Libor’s cessation should be […]

Is SOFR the ultimate replacement for USD LIBOR?
Financial market participants – at least the largest ones – are actively preparing for the expected discontinuation of the London Inter-Bank Offered Rate (LIBOR) after 2021. Transitioning towards a LIBOR-free world is a challenge that requires the involvement and coordination of the whole industry in order to find appropriate solutions to replace the 35 different […]

Introduction of prudential backstops for non-performing loans
Non-performing loans (NPLs) remain at the forefront of the European regulatory agenda, with two major consultations run by the European Central Bank (ECB) and the European Commission (EC) over the recent weeks, both in relation to the introduction of minimum prudential backstops. NPLs, a longstanding hot topic in Europe In the aftermath of the great […]

Is SOFR a strong enough USD LIBOR alternative?
With COVID-19, being declared a pandemic on March 11, 2020, financial institutions have had to shift most of their resources to mitigate the risks that have arisen. This has adversely affected important activities, one of which is market participants’ efforts to detach from LIBOR before its cessation at the end of 2021. As a result, […]

European crisis management framework: ripe for reform?
Since the European crisis management framework was established in 2014, there have not been many failing banks in Europe. However, the recent global health pandemic, combined with the ongoing conflict in Europe between Russia and Ukraine, could easily change this. The EU crisis management framework was established in response to the global financial crisis and […]

Do Asian market Libor preparations pose systemic risk to world markets?
Since Libor was first used in financial markets in 1986, it has become the foundation of the global interbank funding market. However, regulators ruled that Libor’s volatility during the last global financial crisis (GFC) and a rate-rigging crisis in 20121 involving the world’s largest banks exposed a fundamental weakness with the rate’s publication methodology. Yet, […]

IBOR transition: Fallback language developments
The expected 2021 disappearance of LIBOR requires robust fallback language for cash products and derivatives alike. Industry associations have taken initiatives to reform the historic fallback language of securities, with ISDA proactively leading the way on derivatives and national working groups proposing enhancements for cash products. While the derivatives market is expected to be harmonized […]

An interview with Ian-Edward Stafrace of Atlas Insurance PCC : Embracing and enabling insurance disruption
As chief risk officer and executive committee member of Atlas Insurance PCC, Ian-Edward Stafrace is passionate about effective enterprise risk management and seeking opportunity from risk. Here Alan Craig and Enrico Federici of Mazars in Malta, talk to him about technological, regulatory and business model changes and how protected cells are enabling innovation. What do […]

ARRC acts for a smooth IBOR transition
The Alternative Reference Rates Committee (ARRC) continues to support market participants in their efforts to transition from USD London Interbank Offered Rate (LIBOR) towards the Securities Overnight Reference Rate (SOFR). Following the Financial Conduct Authority’s (FCA) March 2020 statement that the expected LIBOR cessation deadline remains unaltered – i.e. end of 2021 – ARRC published […]

Cryptoassets: Accounting for an emerging asset class
The sweeping growth and prolific collection of technologies that make up cryptoassets today have made it incredibly challenging for regulators worldwide to standardize and issue authoritative guidance. Professional accounting standard-setting bodies, like the Financial Accounting Standards Board (FASB) and the International Accounting Standards Board (IASB) are certainly no exception. What started out as just bitcoin […]

Progress on transitioning to SONIA
The Risk-Free Rates Working Group (RFRWG) published an update on the impact of COVID-19 on the timeline for firm’s plans to transition away from GBP LIBOR on the 29th April. While the central assumption of LIBOR’s publication being ceased after the end of 2021 remains intact, the Working Group has amended the timeline for the […]

IBOR reform moves forward, but challenges remain
A raft of recent consultations on Ibor reform indicates that we may finally be making some progress. We have seen the International Swaps and Derivatives Association (ISDA) issue another round of consultations for Inter-Bank Offered Rates (IBORs) trying to solve the issue of the spread and term adjustments in fall-back for derivatives referencing IBORs and […]

Prudential risks for banks with a Russian presence
The invasion of Ukraine by Russia on 24 February 2022 is considered the most significant geopolitical event since the Second World War. While there is no question of military intervention by the European Union (EU) at the moment, the EU has nevertheless decided on a major package of sanctions that will have a heavy impact […]

NPL secondary market may solve the increase in credit risk
The identification and management of non-performing loans or NPLs as early as possible by banks are among supervisors’ current high-level priorities. Indeed, when prudential, monetary, and fiscal crisis mitigation mechanisms are tapered, the weakening of borrowers’ creditworthiness could materialise, along with increasing credit risks and therefore NPLs. This expected rise of new NPLs in European […]

Russian sanctions: what implications for financial institutions?
Following Russia’s annexation of Crimea in March 2014, the United States (US) and the European Union (EU), together with other countries, imposed mainly economic sanctions on Russia. Since Russia’s recognition of the self-proclaimed autonomous republics of Donetsk and Lugansk, followed by Russia’s attack on Ukraine on 24 February 2022, these sanctions have taken on new […]

Eligibility ratios in the insurance sector: improved practices based on recommendations issued by regulators
2023 marks the second year in which insurance and reinsurance companies have published their eligibility ratios for the European Green Taxonomy. For the insurance sector, the objective is to measure the proportion of investments, as well as the proportion of gross premiums collected in non-life insurance, dedicated to financing economic activities in accordance with the […]

Harmonisation of internal model approaches, a new era for banks?
Basel 4 and Single Supervisory Mechanism act to reduce the excessive variability in the results of internal model approaches to credit risk. For more than ten years, Basel reform has encouraged the development and use of internal models designed to better place risk management at the heart of banks’ control arrangements. Basel II saw massive banking […]

European green taxonomy eligibility ratios in the banking sector
The implementation of the European Union’s ‘Taxonomy’ regulation, which integrates two climate objectives, was carried out on 1 January 2022 through the ‘Climate’ Delegated Act released in April 2021. In line with this, the banking sector has been provided with corresponding regulations, allowing banks to measure the portion of their financing dedicated to sustainable economic […]

The use of Big Data tools to improve the effectiveness for AML/CFT and KYC policy
A series of initiatives designed to help combat terrorism financing have put electronic payment cards in the spotlight due to the fact they guarantee anonymity in the use of small sums. Announced on 23 November 2015, these initiatives supplement the action plan for combatting the financing of the terrorism presented by the Minister on 18 […]

How financial institutions can move sustainability reporting to real-world application
The increased demand for sustainable finance shows that awareness of environmental, social and governance (ESG) issues is generally high among financial institutions. Indeed, for many of the larger players subject to the EU’s Non-Financial Reporting Directive (NFRD), there has been a requirement to include ESG information in annual reports for some time. Others have incorporated […]

Diversity in forward-looking macroeconomic scenarios
Under IFRS 9, forward-looking information is a key component of Expected Credit Loss (ECL) calculations. However, forward-looking information requires a significant level of judgement, making comparisons difficult to navigate. Indeed, similar to the use of post-model adjustments, forward-looking scenarios have also been reported by stakeholders in the context of the IFRS 9 impairment post-implementation review […]

Bank credit risk trends show a relative decrease in high risk exposures
Despite banks emerging from the Covid-19 crisis in reasonably good health, the war in Ukraine combined with a global energy crisis and an uncertain economic landscape have once again put the spotlight on credit risk exposures. To better understand credit risk trends, Mazars conducted an analysis of 26 banks in 11 European countries in May […]

EU bodies update country lists of uncooperative and high-risk countries for financial services
Revised list of uncooperative countries and territories for tax purposes published by the European Council The list of uncooperative countries and territories about tax is an important part of the external tax strategy of the EU. Globally, this strategy intends to contribute to the ongoing efforts to advance good governance practices in the tax domain. […]

New reports on transaction monitoring systems and risk analysis published by the ACPR and COLB
ACPR publishes report on automated AML/CFT transaction monitoring systems In 2022, the ACPR conducted a comprehensive thematic review, focussed on the automated systems utilised by the entities under its supervision. This entails entities implementing their obligations in terms of transaction monitoring. The primary objective of this review was to assess the efficiency of the operation and […]

Change in French regulatory landscape for electronic money issuers
The number of electronic money players in the European market has increased in recent years, from 4 in 2010 up to 48 in 2014*. Add to this the fact that numerous players beyond the banking world have also created their own electronic money institutions, including Leetchi, Google and Amazon and the sector is now seen […]

The return of inflation: what consequences for banks?
For several months now, we have been in an economic and financial environment that we have not seen for some years. In May, inflation in the Eurozone reached 8.1%, with six countries exceeding 10%, while the United States recorded an 8.6% year-on-year price increase. The short-term reasons for the return of inflation are well known, […]

ICAAP / ILAAP: what will change in 2016?
Banks prepare for the reinforcement of prudential supervision via the Single Supervisory Mechanism (SSM). After successive waves of new regulatory requirements in recent years, the outlook for the calculation of risks and Pillar 1 capital requirements is becoming clearer. At the same time, whereas the implementation of these new requirements has and continues to mobilise […]

EU regulatory framework on the establishment of the digital euro: from investigation to realisation
With the approaching end of the investigation phase of the ECB’s digital euro project in October 2023, and the expectance of a decision on starting a realisation phase by the end of this year, the pros and cons of a potential digital euro have been widely discussed in the past months. The topic became even […]

Can BIS develop a cryptoasset regulatory framework without limiting the innovation process?
In summer 2022, the Bank for International Settlements (BIS) published its second consultation paper on the prudential treatment of cryptoasset exposures. The guidelines outlined in the proposed document follow an initial discussion paper released in 2019 and a first consultative document issued in 2021. The complete text is set up as a new standard to […]

The digital euro as we know it today
“I see digital as the future of finance”. These are the words of the Executive Vice President of the European Commission (EC), Valdis Dombrovskis, voiced in the summer of 2020. He has undoubtedly been proven right as governments and central banks around the world have heightened their efforts to keep oversight of the digital transition […]

The EBA publishes new report and guidelines in response to risk within the financial services sector
New report on AML/CFT risks in payment institutions In accordance with the European Union regulations, the European Banking Authority (EBA) has been mandated to assess the management of the most significant risks in the fight against money laundering and terrorist financing (ML/FT). The entity’s analysis is centred around the identification and management of ML-FT risks […]

What’s driving financial firms’ sustainability strategies?
To adapt to the swiftly evolving regulatory landscape and meet stakeholders’ expectations, financial firms are increasingly formulating sustainability strategies to address environmental, social and governance (ESG) factors. Notably, emissions reduction and the pursuit of net-zero targets have become central elements of ESG strategies for many financial firms, according to the latest Mazars’ survey Sustainability practices stocktake: […]

Navigating challenges in the retail digital euro landscape
Last October, the European Central Bank (ECB) initiated the preparation phase of the Digital Euro project, following two years of investigation and a proposal on the establishment of a digital euro published by the European Parliament (EP) in June 2023. In January, the ECB began seeking potential providers to develop a digital euro platform and infrastructure […]

Impacts and consequences of the war in Ukraine for banks and insurance companies
The war in Ukraine, as well as the unprecedented sanctions imposed by the European Union, the United States and their partners against Russia have had major consequences for financial services institutions. For foreign companies operating in Russia or Ukraine, the first concern was the safety of their staff. They had to make difficult choices to […]

European Commission to strengthen regulatory framework for bank crisis management
The European Commission published on 18 April 2023 a new legislative package aiming to adapt and strengthen the framework for crisis management and deposit insurance (CMDI), with an acute focus on small and medium-sized banks. This proposal, which follows the announcement of the Eurogroup finance ministers inviting the Commission and the European co-legislators to review […]

Implications of the Revised Banking Chart of Accounts for the West African Financial System
Reforms to an accounting system that has been in force for nearly 20 years will help to increase the security and robustness of the West African financial system, while improving the quality of financial reporting. The Revised Banking Chart of Accounts has been adopted by the monetary authorities in the course of convergence towards Basel […]

Creating a Digital Map for Unclaimed Policies
3 Questions to Mister Doe When it comes to the administration of dormant bank accounts and unclaimed life policies, the quality of data, the inflexibility of internal procedures and complex processing is causing banks and insurers big problems. Vladimir Nguekam, CEO of digital analytical firm Mister Doe talks to Mazars about how taking a digital approach […]

Rethinking Compliance for the Protection of Personal Data
A holiday photo on Instagram, a “like” on Facebook, a PayPal transfer to pay for your Airbnb, or just a bank card payment or an ATM withdrawal: every day, we feed data into greedy and enthusiastic algorithms that are gathering our personal information. A new European regulation adopted in response to this irrational frenzy, the […]

Action Plan for Banks in the West African Monetary Union
A new prudential framework applicable to banks and credit institutions in the West African Economic and Monetary Union (WAEMU) is set to come into force on 1 January 2018. However, a significant delay has been observed in implanting reforms in the majority of banks, where the scale and implications of the necessary work are widely […]

Let’s make the regulatory capital rule simple
On September 27, 2017, the Federal Reserve Board, the Federal Deposit Insurance Corporation and the Office of the Comptroller of the Currency (the “Banking Agencies”) issued a proposed joint rule to simplify several requirements in the Banking Agencies’ regulatory capital rule for banks. The proposed rule would apply only to banking organizations that are not […]

Digital Banking: Lessons from Millennials
By 2025, The Wall Street Journal ([1]) estimated that Generation Y, also known as Millennials, would represent nearly half of the total active population in the world. The challenge for banks is to adapt their strategy to match Generation Y consumer habits and behaviours. Unlike previous generations, Millennials have the increased ability to choose between […]

The clock is ticking
In August 2017, S&P Global Market Intelligence published an analysis of where banks will set up their European hubs. Germany, namely Frankfurt and Berlin, came first with 13 financial institutions. Dublin came a close second attracting 12 banks, insurers or asset managers. Luxembourg, France, the Netherlands and Belgium will also take a share. A bit […]

The Six Key Themes of Internal Governance Harmonisation
As recent as 26 September 2017, the European Banking Authority (EBA) under the Directive 2013/36/EU published its revised guidelines on harmonising the internal governance arrangements of banks across the European Union. The EBA Guidelines will apply as of 30 June 2018 to competent authorities across the EU, as well as to institutions on an individual […]

Could regulation play a role in transforming the FinTech business model?
One of the main differentiators FinTechs have is their current positioning within the financial services value chain ecosystem: they focus on customer experience while their operations execution and control activities are often outsourced to banking institutions. However, is this likely to remain given the increasing interest regulators are paying to these new industry players? While […]

PSD2 supersedes PSD1 on 13 January 2018: comply with the minimum requirements or embrace the future?
PSD2 will supersede PSD1 on 13 January 2018, retaining key benefits from PSD1 such as increased competition with facilitated market entrance for regulated non-bank players, improved economies of scale, enhanced transparency, but also incorporating technological innovation, enhancements and protection into law. This will ensure that a competitive playing field continues to develop, without exposing individuals, […]

Permanent tsb: Digitalisation’s role in the ethical banking mix
The arrival of technology has been a game changer for Ireland’s banking industry. Niall O’Grady Commercial Director of permanent tsb (PTSB) talks to Liam McKenna Partner Consulting Services – Mazars Ireland, about how the bank is using digitalisation to create more meaningful relationships with customers. Liam McKenna: Where does technology fit into PTSB’s proposition – as an […]

Risk culture and supervision: beyond the box-ticking exercise, striving for fair balance
Since the 2008 crisis, the financial sector has been under scrutiny. Identified as one of the crisis root causes, the importance of risk management framework and risk culture and its interconnectedness to ensure the long run financial stability of each organisation has been revealed. Accordingly, institutions are expected to develop an effective risk management framework […]

Will the emergence of big data analytics lead to a new wave of regulation in the financial sector?
Big data analytics is one of the most discussed topics in the world of finance. Application of these methods has led to better assessment of credit quality, improved pricing of insurance contracts as well as automation of client interaction. Processes that were previously cumbersome, such as customer on-boarding, have been streamlined and their costs drastically […]

BEAT Could Eat Into Income Tax Savings
Tax legislation generally includes promises to simplify the process of computing taxes. But in the process of transforming legislation into law, those good intentions often are overshadowed by new complexities. The Tax Cuts and Jobs Act of 2017 is no exception, especially for U.S. multinational corporations. Although most corporations herald their much lower 21% tax […]

Looking ahead – ECB and NCA focus 2016, and what does it mean for the market participants?
The last five years have been a time of much challenge and change for the Central Banking Fraternity in Europe. Crisis, both economic and political, has been followed by much adjustment and change, including both practical economic and policy interventions, structural change in the form of Banking Union, much new regulation and most recently the […]

IFRS 17 poses new challenges for the reinsurance industry
After many years of development, in May 2017, the International Accounting Standards Board (IASB) published a new standard for insurance contracts. Coming into effect on January 1st 2021, the IFRS 17 standard introduces a new model for accounting and measuring insurance liabilities with a framework which is substantially different from current accounting practices. While the […]
President Trump Signs the Senate’s Banking Regulatory Reform Bill (S.2155)
S.1255 the Economic Growth, Regulatory Relief, and Consumer Protection Act (the “Senate Banking Bill”) was passed on March 14, 2018 after a strongly bipartisan 67-31 vote. On May 22, 2018, the House passed the Senate Banking Bill with 258 yeas (225 Republicans and 33 Democrats) and 159 nays (1 Republican and 158 Democrats). The bill […]

Sizing Up Amazon Web Services
Fintech is prominent in today’s business lexicon, having migrated from the back office to a prominent position in both consumer and commercial finance. Its core functionality on mobile devices and wide application in artificial intelligence (AI) spans blockchain, smart contracts, banking, insurance, regulation and cybersecurity. And Amazon Web Services (AWS), a major cloud player, is […]

Podcast: Basel III Implementation – May 2018
In this podcast, Greg Simpson discusses the Prudential Regulatory changes proposed by Basel 3. Together with Phuong Gomard and Bowen Lu, regulatory specialists in Mazars’ Banking Consulting practice, they highlight the impact on the standardised approach to credit risk and operational risk. Whilst relevant to all UK banks, it is particularly relevant to smaller challengers and […]

GDPR and PSD2: what are the issues for FinTechs?
The FinTech model is reaching a new level of maturity. The first stage saw them disrupt the traditional banking business models using technology to impact the customer experience and relationship. The second wave offers FinTechs the opportunity to expand their service offering and develop their independence, provided that they understand their relationship with the regulatory […]

How companies in the financial services sector can measure their human rights footprint in four steps
The complexities of creating and implementing a due diligence framework to monitor and measure the impact financial services have on human rights can be overwhelming. The EU recommended UN Guiding Principles on Business and Human Rights Reporting Framework (www.UNGPreporting.org) – co-authored by Mazars and Shift – , as well as the EU Non-Financial Reporting Directive […]

US Tax Reform: Tax Cuts and Jobs Act Imposes New Limitations on Deductibility of Trade or Business Interest
The Tax Cuts and Jobs Act (the “TCJA”), signed into law in December 2017, and applicable to taxable years beginning after December 31, 2017, contains several provisions that will have a significant impact on specific types of entities and investments. One of the most radical departures from current law involves new limitations on the deductibility […]

Whistleblowers: a path to combatting fraud
While whistleblowing laws and initiatives might differ from country to country, whistleblowers in the financial industry are now well recognized and have gained international attention. Here we analyse the steps taken in the USA to strengthen whistleblowing procedures and practices. Recent allegations of impropriety on several levels have rekindled whistleblowers as a mechanism for identifying […]

FRTB: has the journey finally begun or has it just ended?
It is truly amazing the turmoil 88 pages can produce. Yet while the whole Banking Industry is strongly opposed to some of the new Fundamental Review of the Trading Book (FRTB) requirements, such as the Profit & Loss Attribution (PLA) test, could the EU Council now be considering to only include reporting requirements in CRR2? […]

SFCR: Review of narrative reports, good practices and EIOPA recommendations
The Solvency II Directive increases the requirements for transparency vis-à-vis both the regulatory authorities and the stakeholders, including policyholders, financial analysts and investors. In this context, insurance undertakings and groups were, for the first time, required to publish a narrative report no later than 19 May 2017, known as the Solvency and Financial Condition Report […]

Quantified impacts of IFRS 9 : initial findings
At the end of February 2018, all the major European banks published information on the impact of the implementation of the new standard IFRS 9. IFRS 9 introduces numerous changes (classification, impairment, hedging, etc.). Their impacts at the transition date vary widely from one bank to another. They are negative in most cases, but for […]

Ultimate Forward Rate (UFR): Why we are seeing a change to the rate curve
On 6 February 2018, EIOPA published its latest risk-free interest rate curve to be taken into account for the purposes of Solvency II calculations. Based on calculations for January 2018, the curve is slightly different from previously published curves. This is reflecting significant changes in the long-term expectations of interest rates in recent years which calculates […]

Tackling the issue of NPLs: a European perspective
Because of the 2008 financial and economic crisis, banks have accumulated billions of non-performing loans (NPLs) on their balance sheets. Even 10 years after this major economic event, the situation is not yet back to normal in some countries. In the European Union, and in the Eurozone particularly, NPLs are a real concern as they […]

A good bank requires good supervision
To be a ‘good bank’, a bank must be efficient, innovative and trustworthy. Given its central role at the heart of the economy and financial system and the risks associated with fulfilling its role, banks have to operate within an environment subject to laws, regulations and directives. Outcomes can often be subject to the constraints […]

Simplicity is a complex issue
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed vehicula sem rhoncus quam suscipit convallis. Quisque eu nulla blandit nibh rutrum convallis. Nullam rhoncus dapibus ex.
How Innovation is revolutionising the payments landscape
Financial Technology (“Fintech”) companies have kick-started a revolution in the payments landscape. Using state-of-the art technology, fintech companies are transforming how payments are transacted and processed. Banks and traditional payment providers are having to entirely rethink their approach to how they interact with innovations in order to stay on top of their game. Technological change […]

Managing Operational Risk
In recent years, we have seen a tremendous surge of interest in measuring and managing operational risks, both as a result of regulatory developments in corporate governance and capital adequacy, as well as due to a growing realisation that an enterprise-wide view of risk management is simply good business (those familiar with ISO9001 Quality Management […]

Regulatory reform in uncertain times: no rest for the weary
Despite “reform fatigue” and squeezed profit margins, financial services firms are dealing with a continued flood of regulation. Some are turning to new technologies for compliance help. In this article, written by the Economist Intelligence Unit and sponsored by Mazars, we explore regulatory change in the financial services sector and the impact that it has […]

Podcast: Banking Regulatory Outlook
Along with Mazars banking regulatory advisory specialists Pauline Pelissier and Audrey Cauchet, Greg Simpson provides an overview of the banking regulatory outlook in the UK and Europe over the next 12 to 18 months. They also discuss IFRS9 in the context of regulatory treatments, credit risk management, non-performing loans, CRD5 and CRR2. Podcast player

PSD2, FinTechs and Brexit: The Wider Implications
UK Banks are already gearing up for the introduction of the revised Payment Services Directive (PSD2) that comes into force in January 2018. By providing clear guidelines and regulations, the Directive essentially removes the barriers to new players and opens the doors to FinTechs bringing new products and services to the electronic payments market. While […]

Brexit : Five Key Insights for the global Real Estate sector
Following the UK’s landmark referendum decision to leave the European Union, real estate investors have been dealing with the push and pull of post-Brexit market sentiment. Initial panic surrounding the outcome of the vote saw a raft of UK-based fund managers suspend redemptions from property funds worth £18bn[1] as investors looked to exit the asset […]

New York Proposes Cybersecurity Regulations for Financial Services Companies
New York Department of Financial Services (DFS) has significantly raised the bar for cybersecurity programs, releasing regulations on September 13, 2016 slated to go into effect on January 1, 2017. The regulation will affect all entities with a DFS “license, registration, charter, certificate, permit, accreditation or similar authorization under the banking law, the insurance law […]

SEC Adopts Amendments to Investment Adviser Act Rules
On August 25, 2016, the Securities and Exchange Commission (the “SEC” or the “Commission”) adopted amendments to various rules under the Investment Advisers Act of 1940 (the “Act”). The amendments will be effective 60 days after the date of publication in the Federal Register, but investment advisers are expected to comply with the amendments after […]

Creating a More Homogenous Financial Reporting Platform: An Interview with Javier de Frutos, Chairman of EFFAS
Financial reporting is witnessing a period of evolution as the needs of users become more complex. Javier de Frutos, Chairman of the Commission on Financial Reporting of the European Federation of Financial Analysts’ Societies (EFFAS) and CIO at the investment firm Sailbridge Capital in New York talks to Mazars about his thoughts on the direction […]

100 Days Post Brexit Referendum – How much smarter are we?
Saturday 1 October marked the 100th day since the result of the UK referendum to leave the European Union became known. And it seems neither the British nor their European neighbours have fully come to terms with the idea of a European Union without the UK. Yes, all continental Europeans love British eccentricity: driving “on […]

Brexit : Insights for the Real Estate Sector in the UK
Following the UK’s landmark referendum decision to leave the European Union, real estate investors have been dealing with the push and pull of post-Brexit market sentiment. Initial panic surrounding the outcome of the vote saw a raft of UK-based fund managers suspend redemptions from property funds worth £18bn[1] as investors looked to exit the asset […]

Brexit : Insights for the Real Estate Sector in Germany
In the second of our blogs looking at how the UK’s decision to exit the EU is impacting key real estate locations, our experts shine a light on some of the challenges facing German real estate investors, as well as the potential for greater breadth and depth of real estate opportunities going forward. Berlin: Strong […]

Brexit : Insights for the Real Estate Sector in France
In the third of our blogs looking at how the UK’s decision to exit the EU is impacting key real estate locations, our experts outline some important post-Brexit political and practical considerations for French real estate investors. Need for visibility as political issues take centre stage It’s looking increasingly unlikely that real estate investors will […]

Brexit : Insights for the Real Estate Sector in the USA
In the fourth of our blogs looking at how the UK’s decision to exit the EU is impacting key real estate locations, our experts in the US outline how the current lack of clarity opens the door of opportunity for investors who currently have capital to deploy. Uncertainty also brings opportunity for real estate investors […]

BCBS’ amendments on Simple, Transparent and Comparable (STC) securitisations
As implied in the BCBS consultative document on November 2015, the BCBS published new standards on 11 July 2016 to include amendments on STC securitisations and thus make its final decision for their calibration. The securitisation framework was highlighted in the 2008 financial crisis because of the major role of subprimes in the collapse of […]

Brexit – playing for a draw?
On 20th October, I was delighted to chair an event in collaboration with OMFIF on the implications of Brexit for the financial services industry. We had an excellent panel of experts representing banks and asset managers as well as the City of London in general. The event was badged as a 100 days post referendum […]

FCA data reveals 5,500 UK Companies make use of passporting rules
Brexit continues to be omnipresent. From British Airways’ Business Life (September 2016 p. 11-12, “Post Brexit, Brand Britain must show its mettle… and its sense of humour”) to the Spectator, articles are a mixed cocktail of seeing Britain great again to worries about what’s next. It really depends on the lens through which you are […]

Brexit and China: a mountain to climb?
Over a beer with David Cameron in October last year, Chinese leader Xi Jinping expressed a very clear opinion on which way he wanted Britain’s vote on Brexit. He wanted a “prosperous Europe and a united EU” with the UK firmly in the EU. Britain certainly reached out to China during the last period of […]

BREXIT! – Not GREXIT?
Greece’s financial systems have been tightly monitored by the institutions – once called the Troika – of ECB, IMF and EU Commission in recent years. The systemically relevant Greek banks are under close control of the Joint Supervisory Team (JST), consisting of staff from the European Central Bank and members of the Bank of Greece, […]

Three Key Elements for Building an Effective Human Firewall
Cyber attacks aren’t just getting more frequent, they are also becoming significantly more vicious and sophisticated. According to the latest figures from the Ponemon Institute, the average cost of a data breach has reached nearly $6.5 million in the US, alone. Yet today’s cyber attacks have far-reaching negative impacts that continue to ripple outward long […]

Italian banking – a Brexit-fueled calamity
Brexit continues to dominate the political and financial world across Europe and beyond as people wrestle with its impact. But there’s another massive storm on the horizon for the EU that has been brewing for some time and Brexit may well have brought forward its impact: The Italian Banking Crisis. As reported in the Wall […]

Optimizing claims: a Big opportunity for Big Data Advanced Analytics
Thanks to Advanced Analytics, insurance providers can bring claims management into a new era by combining automatic processing of large volumes of data with human expertise. Analyzing data in order to optimize the claims processing chain is not a new phenomenon for insurance providers, notably in the field of health care. The health care sector […]

Are you prepared? New York State issues new BSA/AML/OFAC transaction monitoring and filtering program regulation
Recently released guidelines require institutions to adopt risk-based programs to monitor and filter transactions for potentially suspicious activity. Beginning January 1, 2017, financial institutions registered under the New York banking law are responsible for complying with anti-terrorism transaction monitoring and filtering program regulations, established by the New York Department of Financial Services (NYDFS). Last month, […]

Brexit: opportunities for smaller overseas banks
The impact of Brexit on foreign banks, and especially the larger ones, has already been the subject of extensive media coverage and speculation. Discussions on the advantages and disadvantages of Brexit for larger overseas banks have been wide-ranging. Will the uncertainty over business models be solved in the short or mid-term? Would relocation bring cost […]

Ifs and Buts
The Brexit debate last week was overshadowed by Theresa May becoming the UK’s new Prime Minister and some of her more radical appointments to her Cabinet. On top came the horrific terror attack in Nice and the failed coup d’état in Turkey. Understandably, the core Brexit debate did not take centre stage but instead provided […]

Making Big Data Work
The unique business transformation attached to the digital era requires companies to respond with velocity. New systems integrating core transactional assets with mobile and social media have to be used – implying their ability to face volume. Moreover those new systems need to manage enriched operational reality and risks. Laurence Malroux, CEO and President of […]

Data governance : the key to reconciling contradictory requirements
Confronted with legislation that is becoming increasingly constrictive, banks must optimize the management of their data. It’s a challenge that is compounded by the fact that data is often dispersed throughout information systems – a fact that aggregators are capitalising on to offer new multi-bank applications. Banks have a role to play in detecting abnormal […]
The Emergence and Significance of ‘FX GLOBAL CODE-2017’
The FX Global Code (Code) was finally published by the Foreign Exchange Working Group (FXWG)[1] on 25th May 2017, clearly laying down the guidelines for good practices in the FX Wholesale marketplace. With numerous scandals causing turbulence in the FX marketplace in the past, it was deemed necessary for global bodies to roll out a […]

Unilateral deregulation by the USA would lead banks to seek new trade-offs
Solvency, liquidity, transparency and oversight requirements: as the Basel Committee meeting in Santiago, Chile in November 2016 demonstrated, there is still much to be discussed on the finalisation of the Basel III agreements. However, the inauguration of the new President of the USA could change the condition of the international dialog. Some might decide to […]

Digital Finance : Meeting Ethics and Compliance Challenges in Financial Services
We recognise digitisation as an important topic for the financial services industry; for this reason, we have developed a content programme with the Economist Intelligence Unit that focuses on how Financial Services companies are adapting their risk and reporting procedures to the new digital environment. This unique programme of thought leadership examines the new challenges in […]

Brexit: the resilience of the infrastructure sector
In previous weeks, I have commented mostly on early signs and emerging risks in the banking sector, including some early warning shots in the property space in particular. But banks and funds invest in many other types of assets and one sector – infrastructure and energy – may even be feeling some benefits from Brexit. […]

Asset Management sector under scrutiny from UK regulator
The Asset Management industry is positioned to be the main focus of the Financial Conduct Authority (“FCA”). On 28 June 2017, the FCA published the final report of its Asset Management Market Study. This follows on from the interim report published in November 2016. In the publication, the FCA has highlighted a number of pertinent […]

The marriage of high tech and high finance
The lines between financial services and high technology are becoming increasingly blurred. Four major technological changes will disrupt financial services in the years ahead. In this article, written by the Economist Intelligence Unit and sponsored by Mazars, we are discussing how technological disruptors are impacting the global financial services industry. We review how C-suite financial services executives, […]

How insurers can make sense of risk
With Solvency II fully in force, the insurance industry has entered a new phase of transformational development. For many insurance companies, Solvency II has provided the opportunity to make better sense of risk and yet, insurance companies continue to operate using risk management programs that have not evolved and may not protect them from the […]

Podcast: Why banks need to address cyber security
In this podcast Greg Simpson discusses cyber security with our expert Francisco Sanches. They discuss major threats such as emerging risks, FCA guidance on cloud data storage and the cyber security skill gaps to name a few. Podcast player

Banks: Five Tactics to Survive Fintech Disruption
The revised Payment Services Directive (PSD2) that comes into force in January 2018 will essentially remove many of the barriers to new players looking to enter the payments market by providing access to customer data and accounts through an EEA wide common legislative platform. Already under pressure from regulatory change and increased competition PSD2 is […]

Podcast: Implications of Banks Implementing IFRS 9
Greg Simpson, Head of Banking UK and banking experts Paul Hodgett and Pierre Latrobe discuss the implications of IFRS9, more specifically they share some of their experience on helping banks implement IFRS 9. As the standard starts on 1 January 2018, they will also comment on some of the areas that banks need to consider […]

New constraints threaten the future of internal model approaches
At the same time as regulators as a whole express their support for the harmonisation, transparency and comparability of banking models at the European level, a new consultative document published by the Basel Committee on 24 March 2016 partly calls into question the use of internal model approaches when evaluating credit risk. The release of […]

Latest consultation puts systemically important banks (G-SIBs) under the microscope
On 6 April 2016, the Basel Committee published a new consultative document outlining revision plans for the calculation of the leverage ratio and submit proposals for additional requirements applicable to systemically important banks (G-SIBs). This new consultation comes as no surprise. Since 2014 the leverage ratio, calculated by dividing Tier 1 capital by the bank’s […]

Feeling the effects of Brexit
It’s two weeks since the Brexit Referendum and it’s fair to say that its consequences are already being felt. At a broad economic level, sterling has hit a 31 year low and economists have revised down the economic outlook for the UK and the Eurozone. The UK has been downgraded by Standards & Poor to […]

IFRS 9 new provisioning and the phase-in period of regulatory capital: a discretionary approach
In about nine months, IFRS 9 will replace IAS 39 and the new accounting environment won’t be the only element to be impacted. In recent months, the Basel Committee on Banking Supervision (BCBS), the EU Commission and the European Banking Authority (EBA) have also been tackling the impact of the new IFRS 9 provisioning on […]

A closer look at the factors underlying the decision to sell NPLs in Italy
There is a clear pipeline of jumbo disposal Non-Performing Loans (NPLs) in Italy, thanks to the ECB push, however vendors will need to take into careful consideration a few factors in their decision, such as recent regulatory reforms of insolvency and foreclosure and a possible EU bad bank. 1. ECB Push Europe’s NPL assets are […]

Capital Markets Union: The Impact on Banks
Business funding diversification, helping to increase options for savers and making the economy more resilient are some of the main objectives set out in the European Commission’s Action Plan on Building a Capital Markets Union (CMU) published on 30 September 2015. While a better spread of financing sources over the capital markets, insurers, households and […]

Infrastructure Investments: the Impact on Solvency II Balance Sheets for Insurers
Background and issues The Cambridge dictionary defines ‘infrastructure’ as ‘the basic systems and services that a country or organisation uses to work effectively’. This rather broad definition covers a wide range of assets at the heart of economic activity: they do not just provide a service to an individual or enterprise, but to economic agents […]

Do Androids Dream of Stock Prices?
We look at the rise of ‘robostocks’ and algorithmic trading, and consider the repercussions on financial markets. An old investment adage mockingly states that “a failed trade becomes a long term investment”. The idea behind it is that if a security is bought and underperforms, investors tend to keep it until it eventually becomes profitable, […]

Consolidated Audit Trail Approved by the U.S. Securities and Exchange Commission
The Securities and Exchange Commission (“SEC”) approved a plan on November 15, 2016, to create the consolidated audit trail (“CAT”), a central data source to collect and accurately identify every order, cancellation, modification and trade execution for all exchange-listed equities and options across all U.S. markets. This plan is pursuant to SEC Rule 613, in […]

Empower your people to protect the bank
Cyberattacks aren’t just getting more frequent, they are also becoming significantly more vicious and sophisticated. The majority of today’s data breaches result from human error, making cybersecurity a “people problem” as well as a technology issue. The solution to this people problem can’t be solved by purchasing new hardware or software or implementing sophisticated network […]

Digitalization at the heart of the transformation of AXA Assistance
Digitalization poses many challenges for AXA Assistance as well as bringing great opportunities. Alexis de Schonen, Digital Transformation and Strategy Director, and Roman Puszka, Chief Compliance Officer and Data Privacy Officer, discuss this issue. Does digitalization play a central role at AXA Assistance? And if so, which one? Alexis de Schonen : Digitalization is the […]

Revision of the CRR / CRD IV package
On Wednesday 23 November, the European Commission presented its long-awaited revision of the Capital Requirements Regulation (CRR) and Capital Requirements Directive (CRD IV), including the regulatory changes that mark the finalisation of the Basel III agreements. This revision follows five years of consultations conducted by the Basel Committee. It aims to foster financial stability and to enhance […]
Crypto-Funds: Regulation? Yes please!
While 2018 has witnessed some turmoil in the crypto-currency markets, interest in this new asset class – and also in investment funds which allow easy access to crypto-currencies – remains high. On 26 June 2018 CBOE Global Markets filed an application with the US Security and Exchange Commission (SEC) seeking approval for a Bitcoin Exchange […]

New prudential regulation for investment firms in Europe
At the end of nearly two years of legislative work, the reform of the prudential regulation of investment firms completed its final phase with the publication in the Official Journal of the European Union of two new regulatory texts: Regulation 2019/2033 on the prudential requirements of investment firms (IFR), and Directive 2019/2034 on the prudential […]

European Insurers’ IFRS 9 Benchmark Study
The new standard IFRS 9 on financial instruments has been effective starting 1st January 2018 for most entities but insurance groups have the possibility to defer its application to 2021, the year when the new standard IFRS 17 on insurance contracts will enter into force. IFRS 9 introduces numerous changes (Phase 1/ classification, Phase 2/ […]

Can banks balance the opportunities and challenges of digitalisation?
The Covid-19 pandemic has amplified technology’s impact on the banking sector, helping to prove that technology now stands at the core of business sustainability for banks. In their constant search for convenience, digitally-savvy customers have pushed banks’ focus towards providing global business solutions more than ever. A new normal has emerged: an environment where banks’ […]

Can markets in crypto-assets (MiCA) give banks a regulatory edge?
Crypto-asset markets have been on banks’ radar for some time. While interest and involvement have varied, regulatory developments have been a driving force. In September 2020, the European Union (EU) published a proposal for the regulation of Markets in Crypto-assets (MiCA), offering a uniform legal framework for crypto-assets in the EU. On 14 March 2022, […]

Eurofi financial summit addresses EU’s ecological and digital transition
As a setting for exchange between European Union (EU) economic and financial regulators and senior financial sector executives from the industry, one of the world’s largest financial services conferences, Eurofi, took place in Paris in February. Established in 2000, the Eurofi meetings occur bi-annually* alongside the Economic and Financial Affairs Council configuration (ECOFIN) meetings. The […]

EBA launches a central database for AML/CFT
A central database to strengthen the anti-money laundering and counter-terrorist financing (AML/CFT) framework was launched by the European Banking Authority (EBA) on 31 January 2022. Called EuReCA, the new database will be essential to coordinate efforts by national competent authorities and the EBA to prevent and fight money laundering and terrorist financing (ML/TF) risks throughout […]

France’s EU Council Presidency to focus on new growth model
As part of its rotating Presidency of the EU Council for a six-month mandate, France chaired its first EU Council of Finance Ministers (ECOFIN) meeting on 18 January with a view to getting certain current legislative work finalised. The ECOFIN meeting was mainly dedicated to introducing the Presidency’s roadmap for the months to come. Beyond […]

Positive behavioural and cultural change: the implementation of an accountability framework
As regulated entities execute their post-Brexit strategies and relocate their European Union (EU) operations from the UK to other EU states, a key issue to be addressed for those relocating to Ireland remain to be the impending legislative changes surrounding increased accountability standards for executives and non-executives. Not least, the breaking of the participation link, […]

The long road to proportionality in prudential regulation and supervision
The great financial crisis triggered a massive wave of bankruptcies in the worldwide banking sector, affected not only large international banks such as Lehman Brothers but also local ones such as Northern Rock in the UK. Basel prudential standards are designed to cope with financial risks stemming from the global banking system without taking into […]

Implications of Covid-19 for the LSIs and the supervisory focus: an interview with Patrick Amis, ECB
On 19 January 2022, Mr Patrick Amis, the head of ECB Directorate General Specialised Institutions and Less Significant Institutions (DG/SPL) had a formal meeting with Mazars to discuss the implications of the pandemic for the LSIs and the supervisory focus. The main risks outlined by Mr Amis, were in the areas of NPLs, digitalisation, IRRBB, […]

Quarterly SSM briefing: spotlight on supervisory priorities, banking union and liquidity ratio
Supervisory priorities 2022-2024 In December 2021, the European Central Bank (ECB) and the national supervisory authorities of the Eurozone countries published their supervisory priorities for 2022-2024. The three-year coverage enables the ECB banking supervision to achieve good progress in addressing the identified vulnerabilities while at the same time affording enough flexibility in any corresponding actions […]

Sustainability and climate risk: what can banks expect?
The growing importance of sustainability issues and the role of credit institutions in financing transformation places climate and environmental risks at the core of regulatory and supervisory scrutiny today. For some years now, the Network for Greening the Financial System (NGFS), comprising central banks and national supervisory authorities, has been working to enhance sustainability and […]

New European authority aims to strengthen framework to fight money laundering
The creation of a new Anti-Money Laundering Authority will transform the supervision of money laundering and financing terrorism (AML/CFT) in the EU. Proposed reforms also extend the AML/CFT rules to all crypto-asset service providers, as well as include specific rules concerning due diligence on customers and beneficial ownership. It is expected that some of these […]

New-style cyber insurance policy models on the rise
Regardless of geography or business sector, many groups and companies have taken out cybersecurity insurance policies in recent years. These policies cover companies against new threats to information systems, including ransomware and data theft incidents that have been making the headlines. For a long time, the risks identified in these policies were on the borderline […]

European Commission adopts review of Solvency II
On 22 September, the European Commission adopted a review of Solvency II following the consultation launched by EIOPA in 2020, whose final guidance was published in December 2020. As the Commission notes, the 2020 review of the directive met several objectives: • remove the obstacles to long-term financing of the economy and redirect investment by […]

The FSOC weighs in on climate risk
The Financial Stability Oversight Council (FSOC) was established under the Dodd-Frank Wall Street Reform and Consumer Protection Act as a result of the 2007-2008 US financial crisis. A first of its kind, the 15-member council is tasked primarily with identifying growing systemic risks to US financial stability and proposing coordinated regulatory responses to both preempt […]

Regulated firms: A matter of life and death
As the PRA transitions from a “rule-taker” to a “rule-maker”, small and medium-sized banks operating in the UK can expect to benefit from a more “streamlined” regulatory regime that could be easier to interpret, implement and maintain; but at the same time, they can also expect the PRA to be progressively more involved in scrutinising […]

The road to implementing the final Basel agreements
The unveiling of the new banking package “CRR3 – CRD6” on 27 October 2021 presents a further landmark on the road to implementing the final Basel III agreements. The regulatory scheme will also focus on the revision of the market risk framework from January 2019, as well as the latest developments in pillar 3 requirements. […]

First ACPR climate stress test pilot exercise results
Climate change introduces considerable economic challenges. On the one hand, financial institutions must contribute to the transition to a low-carbon and balanced economy to effectively combat global warming. On the other hand, the financial sector is exposed to climate-related and environmental risks and therefore needs to implement appropriate risk management practices within a financial stability […]

How the new prudential regime will impact EU investment firms notably French
A major step forward has been taken in implementing the European “investment firms” package in France*. The transposition of the package into local legislation, alongside EU Regulation 2019/2033 on prudential requirements for investment firms (IFR), came into full effect on 26 June 2021. In accordance with the proportionality principle, the IFR and investment firms directive […]

How banks can address supply chain risk
Local and international trends have transformed the way banks operate, affecting their capital positions and profitability. In particular, ongoing digitalisation programmes and technological innovation continue to add pressure on traditional banking models, including the supply chain. While management’s focus on capital preservation, profitability and growth for shareholders remains, risks from an operational perspective have intensified. […]

Five steps to transforming banking operating models
With the current ultra-low interest rate environment and market volatility having a negative impact on banks’ returns and, ultimately, their capital positions, operating models must quickly adapt and become more cost-efficient to maintain profitability. This drive for cost-efficiency has become more apparent as innovation in technology and ongoing digitalisation have further upended traditional banking systems […]

EBA: draft technical standards on Pillar 3 disclosures of ESG risks
On 1 March 2021, the European Banking Authority (EBA) launched a public consultation on draft implementing technical standards (ITS) for Pillar 3 disclosures of environmental, social and governance (ESG) risks, under its capital requirements regulation (CRR) mandate. The consultation will end on 1 June 2021. Large banking institutions with securities traded on a regulated market […]

Achieving digital operational resilience
The digitalisation of banking processes and the introduction of AI-led technology impact the central and strategic role of information systems within the banking system. The growing use of information and communication technology (ICT) exposes all financial institutions to an increasing level of digital risk that could weaken their operational resilience, in particular, due to more […]

Sustainable finance regulations signal a sea change for insurance sector
The European Green Deal aims to achieve climate neutrality by 2050 and create a modern, competitive and resource-efficient economy. To meet its objectives, the European Commission has begun to restructure the non-financial reporting requirements for companies. Although some of the requirements were partially implemented in 2021, this is only the beginning of a real sea […]

Solvency II Directive measures to aid European economic recovery
While the European Commission’s most recent opinion on the review of the Solvency II Directive is broadly in line with the final European Insurance and Occupational Pensions Authority (EIPOA) opinion issued in December 2020, some measures have now been amended. These amendments are designed to strengthen the capacity of European insurers to contribute to the […]

Shaping the future of banking with 5G
Over the past decade, the financial services industry has been disrupted by the arrival of new players whose rise to prominence has pushed traditional banks – previously faced with little competition – to transform themselves. In this context, technology and innovation, particularly 5G, will allow the most skilful and agile banking organisations to take advantage […]

Sustainable finance series: Why does sustainable finance matter?
The momentum towards a low-carbon economic system is only set to grow. Financial services firms are pivotal actors in the transition; consequently, increasing demands are being put on them to demonstrate their sustainable finance activities and credentials. This blog explains what sustainable finance is and why it matters to financial services firms. What is Sustainable […]

Unlocking the potential of ecosystems: a deep dive into open insurance and APIs
In the contemporary landscape of insurance, the business model of open insurance, characterised by the strategic opening of insurers’ resources to external collaborators, has been a focal point of discussion. Unlike the banking sector, where regulatory mandates such as the Payment Services Directive (PSD2) of 2018 have compelled the development of open banking practices, insurers […]

Mitigating the financial impacts of climate-related risks
The integration of environmental, social and governance (ESG) considerations into strategic planning is increasingly becoming a common practice among financial services firms. However, climate-related risks can also serve as drivers of financial risk for institutions. These risks can manifest through various transmission channels, translating climate and environmental (C&E) risks into more conventional categories such as […]

How are financial institutions reflecting C&E considerations in risk appetite statements?
There is growing pressure for banks and insurers to incorporate C&E factors in their risk management frameworks (RMF). As a practice, it gives the ability to set clear thresholds for the climate impacts banks and insurers are willing and able to absorb. By establishing these thresholds, firms can effectively monitor their exposure to C&E risks, […]

SSM supervisory priorities for 2024-2026: addressing identified vulnerabilities in banks
On 19 December 2023, the European Central Bank (ECB) published its updated Single Supervisory Mechanism (SSM) strategic supervisory priorities for the period 2024 to 2026. The priorities indicate what banks should expect in terms of supervisory activities in 2024. For 2024-2026, the ECB supervisory priorities are built upon three main pillars: These priorities were informed […]

Transitioning to greener practices in the real estate sector
In 2022, the European Union implemented the green taxonomy for the second year, requiring companies to disclose indicators related to climate objectives. The green taxonomy aims to guide capital investment towards environmentally sustainable activities, making companies assess their alignment with the EU’s sustainable transition and enabling financial institutions to prioritise funding for projects contributing the […]

The Council of Europe provides updates on combatting the financing of terrorism
2022 AML-CFT Committee report available The MONEYVAL Committee, an entity of the Council of Europe which is tasked with addressing challenge of money laundering and terrorist financing (ML/FT), has recently published the AML-CFT report 2022. The findings of the report are primarily centred around adherence to compliance with global sanctions, notably in freezing or confiscation […]

Asset managers and ESG implementation: turning regulatory and operational compliance into commercial opportunities
ESG-related regulatory requirements, and scrutiny, show no signs of abating. Asset managers have a pivotal role in financing the transition towards low-carbon economic systems. Hence, governments have introduced several ESG-related regulatory requirements that apply to asset managers. Some examples of these are the Sustainable Finance Disclosure Regulation (SFDR) in the EU and the mandatory disclosures […]

ESMA’s latest Q&A: which key topics are covered and how has it impacted the AFG?
The European Securities and Markets Authority (ESMA) published on 17 November, together with EBA and IOEPA, a Q&A on the RTS of the SFDR Delegated Regulation (Commission Delegated Regulation (EU) 2022/1288), just six weeks before coming into force. The Q&A clarifies a number of points, including those relating to principal adverse impacts (PAIs) and taxonomic […]

Banking: crisis, what crisis?
The rapid collapse of one of Switzerland’s most emblematic banks, following the demise of tech lenders on America’s west coast, has raised concern over banking stability. What are the consequences for the sector, the economy and for society? Gregory Marchat, Global Head of FS Advisory, and Emmanuel Dooseman, Global Head of Banking and Capital Markets, […]

Governance, operational resilience, and business models remain crucial for banks in an environment of rising rates and digital banking
In an interview, Korbinian Ibel, Director General at the European Central Bank (ECB), shares insight on how bank-specific direct supervision works, what the current risks and challenges are, and priorities to look out for in the coming years. What does the Banking Supervision arm of the European Central Bank do? Find out about its policies, […]

Leveraged transactions: supervisory expectations in the Eurozone
The chair of the European Central Bank’s Supervisory Board, Andrea Enria, has voiced several times in the past months the supervisor’s concern with the increasing growth of the leveraged finance sector, which deals with loans to highly indebted borrowers. By mid-2021, the combination of a strong global loan moratoria policy and the long-standing low interest […]

Climate change valuation adjustment: introducing a climate change scenario extrapolation to long dated CDS curve
The global climate crisis has triggered the financial sphere to address the way in which it conducts business. Climate risk consideration is currently growing in the banking industry but should also be considered by banks in the Credit Valuation Adjustment (CVA) when pricing derivatives. The credit risk for long dated derivatives (beyond 10 years), reflected […]

The Fed shares instructions on its first pilot climate scenario analysis exercise
The Federal Reserve Board (Fed) has shared instructions on its pilot climate scenario analysis exercise (CSA). Six of the largest U.S. banks, i.e., Bank of America, Citigroup, Goldman Sachs, JPMorgan Chase, Morgan Stanley, and Wells Fargo are participating in the exercise and are requested to submit their results along with documentation by July 31, 2023. […]

Why ESG-linked features impact financial assets classification under IFRS?
In our last article on sustainability-linked financing, we highlighted the accounting issues related to these contracts that are currently being debated between stakeholders. The most critical issue is the classification of loans or bonds that reference the borrower or issuer’s environmental, social and governance (ESG) key performance indicators (KPIs) on the balance sheet of lenders […]

Results of the ECB 2022 thematic review on climate-related and environmental risks
The European Central Bank (ECB) has expressed a significant supervisory concern surrounding more than half of supervised banks in terms of the progress made on fulfilling the expectations specified in the Guide on climate-related and environmental risks. The ECB recently concluded its 2022 thematic review of the banking sector’s alignment with supervisory expectations. This review […]

EBA considers bottom-up stress testing with top-down elements
The European Banking Authority (EBA) is tasked, in cooperation with the European Systematic Risk Board (ESRB), to initiate and coordinate biennial EU-wide stress testing exercises to assess the resilience of institutions to adverse market developments. The objective is to provide supervisors, banks, and other market participants with a common analytical framework to consistently compare and […]

IFRS series on sustainability-linked financing
As environmental, social and governance concerns are becoming more and more prevalent, sustainable finance is now under the spotlight. The financial sector has a key role to play in achieving the ESG transition. One of the levies developed by the financial industry is to propose new kinds of financing that promote ESG practices and projects […]

New pilot scheme opens pathway for blockchain technology
A new regulation introducing a pilot scheme based on blockchain technology is set to come into force on 23 March 2023. The new European regulation1 is an experiment to develop secondary markets for financial securities based on distributed ledger technology (DLT). Authorised participants in the scheme will be able to provide trading services and settlement-delivery […]

How to address climate risk in the banking prudential framework
Climate change is now firmly in the focus of prudential regulators and supervisors across the globe. Against this background, the European Banking Authority (EBA) is mandated to assess whether a dedicated prudential treatment of exposures related to assets or activities associated substantially with environmental and social objectives would be justified. Based on its findings, the […]

Quarterly SSM briefing: stable supervisory priorities and the ECB’s green agenda
The last few weeks have been marked by an ongoing review of the supervisory priorities initially listed by the Single Supervisory Mechanism (SSM) for 2022-24, and developments in the climate agenda outlined by the European Central Bank (ECB). ECB’s supervisory priorities for 2022-24 remain stable despite geopolitical instabilities and challenges At the beginning of 2022, […]

The digital euro: the future of central banking in Europe?
Central Bank Digital Currencies (CBDCs) continue to receive increasing attention not only from the ECB but all over the world. So far, 10 countries [1] have already deployed CBDC programmes with another 15 countries [2] currently conducting pilot programmes. In total, 105 countries are considering using CBDC programmes, representing over 95% of global GDP and […]

The Basel Committee: updated guidance on the external audit of banks
Against the background of a new year still severely affected by the persistence of the pandemic throughout the world and economies facing an unprecedented global macro-economic shock, the Basel Committee has felt it necessary to address the audit of the expected credit loss (ECL) accounting estimate within the overall financial statement audit. With IFRS 9 […]

Managing an increase in bank credit risk
While 2020 went relatively smoothly for the banking sector, uncertainties remain on the potential effects of Covid-19 on the real economy. Any negative impact could lead to heavy losses for the sector, especially when support measures are gradually phased out. These measures have not only contained the anticipated increase in credit risks, but have also […]

Integrated Reporting: Towards a Global Adoption?
Integrated Reporting applies principles and concepts that are focused on bringing greater cohesion and efficiency to the reporting process, and adopting ‘integrated thinking’ as a way of breaking down internal silos and reducing duplication.The Framework has been tested and assessed during these past three years and significant ‘breakthroughs’ have been achieved. Our present paper, therefore, […]

Brexit Watch #4 : A snapshot of how the financial services regulators are reacting
Brexit preparation is one of the largest undertakings that regulators and market participants have ever done, considering the uncertainty and the impact it carries. Many financial institutions have stopped waiting for lawmakers to finalise negotiations over the terms of the exit and are already working towards contingency plans. Banks and brokers are setting up new […]

How to predict the results of P&L attribution tests in the FRTB framework?
Under the terms of the Fundamental Review of the Trading Book (FRTB), a bank wishing to apply the Internal Modal Approach (IMA) to calculate its capital charge associated with market risk must carry out: backtesting on the Trading Book (TB) and for each trading desk (TD), two profit and loss attribution (PLA) tests for each […]

The Supervisory Answer to Hong Kong’s Worsening Economic Performance
Pierre Latrobe at Mazars discusses the measures the HKMA has taken so far to strengthen its macroprudential supervisory toolkit and address potential risks to the wider financial system. The Hong Kong economy is suffering from several lingering negative factors, the US-China trade war, the global economic slowdown and the ongoing protests, to name but a […]

Brexit Watch #6: Seeing past the fog of uncertainty – How are the regulators responding?
The British political landscape has been unsettled and uncertain. Boris Johnson defeated Theresa May in July 2019 to become Prime Minister with his “do or die” conviction for the UK’s exit from the EU, with or without a deal. While the Government has been successful in achieving Parliament’s support for a renegotiated withdrawal deal, MPs […]

The Impact of Robotic Process Automation in Financial Services
Robotic process automation (RPA) is software that sits on a PC or workstation and is programmed to mimic the activities that a member of staff would perform. It will open applications, copy and paste data, and follow predefined rules. A robot will complete activities three to five times faster than a person. Customer satisfaction can […]

European CIB firms penalised by their regulatory environment
September 2018 saw the tenth anniversary of the collapse of Lehman Brothers, the US corporate and investment bank that was symbolic of Wall Street. Its failure is still fresh in the mind, and marked a turning point for banking and financial regulation. The disappearance of Lehman launched a cycle of “re-regulation” intended to increase the […]

IFRS 16: Potential Changes in Real Estate Strategies
The standard IFRS 16 on leases is applicable to financial periods current at 1 January 2019. It applies to listed companies, their consolidated subsidiaries and entities presenting their accounts under international financial reporting standards (IFRS). The standard seeks to improve the presentation of leases in the accounts, and requires lessees (tenants) to account for leases […]

Real Estate Data Lake
Mass data… The real estate sector is gradually going digital, and recent constructions now incorporate equipment and connectivity to allow both use and maintenance to be optimised. However, as the renovation of the stock is naturally slow, the majority of these assets are not “connected”. Nevertheless, a great deal of data is available and constitutes […]

Brexit Watch #5: Brexit Extension – How are the Regulators Reacting?
During a meeting of the Special European Council on the 10 April 2019, EU leaders agreed to a flexible Brexit extension until 31 October 2019, to allow for the ratification of a withdrawal agreement. Despite this extension, there is still great pressure on Theresa May to secure a deal before the EU Parliament elections are […]

The need for a consistent agenda between regulators, supervisors and legislators
With 2019 marking a move for the European Banking Authority (EBA) to Paris in April, regulatory priorities will see the EBA preparing the work of transposing the last Basel III agreements. Following a quantitative and qualitative study, the Commission will be awaiting its opinion in or after June 2019. Further, in the context of EBA mandates […]

Implementation of post-crisis reforms and remaining challenges in 2019
At the last G20 summit in Buenos Aires, leaders called for the full implementation of all major international financial reforms intended to improve the financial system, in particular, those drawn up by the Financial Stability Board (FSB) and the Basel Committee on Banking Supervision (BCBS), the last being the review of market risk framework published […]

COVID-19, banks and regulation: the road ahead in the UK and Europe
The Covid-19 outbreak and the unprecedented emergency it presents has created a unique threat to the world’s economy. Like all sectors, banking has been impacted, and its stakeholders have felt excessive pressure over the last few weeks to get things right. Regulators in financial markets around the globe have all announced Covid-19 action plans, which […]

Brexit, Volcker 2.0 and the Bipartisan Banking Bill lead topics of 2019 Institute of International Bankers conference
On March 11 and 12, 2019, Mazars attended the 30th annual conference organized by the Institute of International Bankers (IIB). Agencies and regulators serving as speakers and panelists this year, included: •The Federal Reserve Board (FRB) •The Department of the Treasury •The Commodity Futures Trading Commission (CFTC) •The Securities and Exchanges Commission (SEC) •The Office […]

Data Protection: constraint or opportunity?
Today’s world is witnessing an explosion of data, including personal data: your civil status, what you do and don’t like, your holidays, your favourite leisure activities. The exploitation of all this data is multiplying through the use of innovative IT tools. [pukka_pullquote width=”300″ txt_color=”#ffffff” bg_color=”#2d2d2d” size=”24″ align=”left”]”A pessimist sees the difficulty in every opportunity; an […]

Brexit Watch #3: countdown is on
Following a majority vote against Theresa May’s Brexit deal on 15 January 2019, and with only 3 weeks until the proposed deadline of 29 March, financial services authorities in the UK and EU have been urgently preparing for an increasingly likely no-deal Brexit, announcing further transitional instruments and offering guidance to firms within the sector. […]

Is there light at the end of the Trading Book’s tunnel?
Seven years after the first Basel Committee on Banking Supervision’s (BCBS) consultative paper on the Fundamental Review of the Trading Book (FRTB) and three years after the publication of the revised Market Risk Framework, is the 14 January 2019 release of the final Minimum Capital Requirements for market risk the end of this particular regulatory […]

Climate change: a threat to the stability of the financial services
With rising global temperatures[1] comes an ever-growing pressure on the financial services sector to respond and prepare for the far-reaching effects of climate change. The impacts upon the sector are already being felt – extreme weather events are creating significant losses for insurers and credit risks for banks, and pressures on businesses to demonstrate sustainable […]
A decade on from Lehman Brothers
Which is the more significant – the tenth anniversary of the collapse of Lehman Brothers, or the tenth anniversary of the opening of the App Store? For the global financial community world, 15 September 2008 is a key date, weighted with as much symbolism as the great stock market crash of 24 October 1929 had […]

Brexit Watch #2 : Impact of No Deal and Other Regulatory Issues
In the second installation to our Brexit Watch, the delay of the House of Commons vote and subsequent negotiations increases uncertainty, with multiple possible scenarios set to emerge. Brexit preparation has been one of the largest undertakings for regulatory bodies on both sides of the channel. Despite continued unpredictability surrounding outcomes, new directives and amendments […]

European banks are better armed against macro-economic shocks
On Friday 2 November, as expected, the European Banking Authority (EBA) published the results of the 2018 EU wide stress tests on European banks’ solvency in the event of macro-economic shocks. This was the fourth exercise of the now-biannual testing which has been carried out on European Union banks. Despite more severe tests than in […]

Brexit Watch #1 : Impact of No Deal and Other Regulatory Issues
As negotiations on the UK’s exit from Europe continue, albeit slowly, regulatory bodies in the UK and Europe are beginning to issue regulatory changes to cope with all eventualities, including the UK leaving Europe without a deal. As a result, a number of new directives and amendments to regulations have been issued over the summer […]

Robo-advisors: turbo-charging the race for unit-linked sales?
With a portfolio in excess of €1300 billion in 2017, euro savings are firmly established as the preferred life-insurance product for people in France, thanks to their threefold benefits of guaranteed capital, attractive returns and instant liquidity. However, recent financial and regulatory developments raise questions as to the legitimacy of this product in the savings […]

Study highlights significant variations in HKFRS 9 reporting practices
One year on since the HKFRS 9 standard on financial instruments came into force in Hong Kong and two years since the First Time Application (FTA), trends and insights into impacts of the standard are beginning to evolve. As a reminder, the standard introduced numerous changes with regard to the classification, impairment recognition and the […]

COVID-19: Phase 1 of SFTR delayed
The European Securities and Markets Authority (ESMA) has issued a public statement to announce the delay of the industry’s compliance with phase one of the Securities Financing Transactions Regulation (SFTR). This is in response to ESMA’s awareness of the financial industry’s struggle to devote resources to comply with the new reporting obligation, as firms face […]

The impact of credit risk on 2021 stress tests
On 13 November 2020, the EBA published the final methodological note for the 2021 EU-wide stress-testing exercise. The aim of the stress tests is to assess the resilience of financial institutions to adverse economic and financial developments, in particular in the event of an increase in credit risk due to the default of the borrower. […]

A Tax Playbook for the Digitalised Economy (Part 1)
In a series of articles aimed at promoting debate on the evolution of international tax regimes, Michael Lennard, Chief of International Tax Cooperation and Trade in the Financing for Development Office (FfDO) of the United Nations, discusses the tax-related challenges governments, professionals and practitioners face. In the first of this two-part article, Mr Lennard expresses […]

2021 stress tests planned as banks face worsening crisis
The publication on 29 January of baseline and adverse scenarios, output templates, instructions and market assumptions required to carry out stress tests signals the go-ahead by the European Banking Association (EBA) for the 2021 regulatory exercise. Because of the Covid-19 pandemic, these tests, originally planned for 2020, will take place between now and 31 July […]

Resolvability is now the SRB’s key focus
With the economic repercussions of the Covid-19 crisis yet to be fully assessed, a robust resolution framework is essential to ensure the stability of the banking system. While the banks were given leave to postpone the reporting of some less urgent information in spring 2020, the Single Resolution Board (SRB) has reiterated the importance of […]

Digitalising the real estate industry
While digital transformation has been disrupting all business sectors for many years, 2020 will be remembered for its particular impact on real estate administrators. A third of French respondents believe that artificial intelligence can be more efficient than a real estate agent. Moreover, 40% of those under 50 years old are convinced that the property […]

EBA discussion paper on the management and supervision of ESG risks
European sustainable finance regulations evolved considerably in 2020, and the European Banking Authority (EBA) is continuing this trend into 2021. It recently published a discussion paper assessing the potential inclusion of Environmental, Social and Governance (ESG) risks in the supervisory review and evaluation process (SREP) performed by national competent authorities (NCAs)[1]. What firms need to […]

Can Africa’s banking sector maintain its growth momentum?
With more than half of the world’s fastest-growing economies located in Africa1, the continent’s economic outlook is a positive one. Average annual GDP growth since 2000 is over 5%, placing Africa as the second-fastest growing economy behind Latin America. Real GDP growth, estimated at 3.4% for 2019, is projected to accelerate to 4.1% in 2021. […]

Injecting noise into the discussion
Michael Lennard, Chief of International Tax Cooperation and Trade in the Financing for Sustainable Development Office (FfDO) of the United Nations, examines the role of tax toolkits for developing countries from a personal perspective. The Platform for Collaboration on Tax (PCT) involving the UN, OECD, IMF and the World Bank, is certainly a good example […]

Mazars’ banking regulatory radar: 2020-2025
In this edition of our Banking Regulatory Radar, we cover the key regulatory developments in the banking sector for 2020-2025. The latest version of the Mazars’ Regulatory Radar has been updated with all the Level 2 legislation published in 2020, as well as the measures that were taken in the context of the Covid-19 pandemic. […]

Can regulatory systems come to terms with Facebook’s stablecoin?
Facebook’s ambition to create a transferable global digital coin between users on the social media giant’s messaging platforms WhatsApp and Messenger has been controversial from the outset. Perhaps not surprisingly, the backlash from regulators around the world was substantial from day one. The world’s leading economies were less than enthusiastic of the possibility of a […]

Building a more inclusive tax model
Michael Lennard, Chief of International Tax Cooperation and Trade in the Financing for Sustainable Development Office (FSDO) of the United Nations, discusses, from a personal perspective, a range of key issues on the UN’s approach to transfer pricing. In 2019 the United Nations Tax Committee issued draft guidance on financial transactions. It was finalized in […]

A Tax Playbook for the Digitalised Economy (Part 2)
In a series of articles aimed at promoting debate on the evolution of international tax regimes, Michael Lennard, Chief of International Tax Cooperation and Trade in the Financing for Sustainable Development Office (FSDO) of the United Nations, discusses the tax-related challenges governments, professionals and practitioners face. Following on from the first article on this topic, […]

2021 Stress testing the UK banking system: the Bank of England’s approach
March 2020 marked the first time – since its inception in 2014 – that the Bank of England (BoE) cancelled its annual stress tests for the UK’s biggest lenders. Instead, they undertook a desktop analysis of the UK banking sector resilience. In late 2020, the Financial Policy Committee (FPC) judged that most banks have capital […]

Covid-19: Major risk considerations for the banking sector
As we continue to feel the effects of the global pandemic, the banking sector, like many other sectors, now faces unprecedented uncertainty about the economic outlook ahead. While banks go into this pandemic in a stronger position than the global financial crisis of 2008, the current environment presents particular challenges and disruption to standard accounting […]

UK supervision of international banks post Brexit
Around one-fifth of global banking activity is undertaken in the UK. Almost half of the UK’s banking assets are held by international banks. The PRA currently supervises approximately 250 international banks, both branches and subsidiaries, which are part of around 180 international groups. Background On 11 January 2021, the PRA shared in a Consultation Paper […]

Reducing reporting burden for European banks while increasing data quality: a challenge for the EBA
Under article 430c of the updated Capital Requirements Regulation (CRR 2), the European Parliament and the Council of the European Union mandate that the European Banking Authority (EBA) perform a feasibility study on reducing the reporting burden for the European banking sector while ensuring data collection for monetary policy, resolution and supervisory purposes and take […]

How the insurance industry can emerge stronger
There is little doubt that Covid-19 has had a significant impact on insurers, but there were already factors in play that were adding pressure on the insurance industry. What covid-19 has done is to create new challenges, as well as bringing existing challenges to the foreground. Looking ahead, the actions insurers take now to deal […]

Addressing the challenges of the new sustainable finance regulations
As the world gears up for the transition to net-zero, the European Union is setting ambitious targets with respect to its own environmental footprint. For instance, by 2030 the EU is looking to reduce European greenhouse gas emissions by at least 55% compared to 1990 levels; increase the share of renewables within Europe’s total energy […]

Acceleration in changing the prudential treatment for Software Assets: Covid-19 impact
Over recent years, technology and software have become strategic assets for competitiveness and resilience in the banking sector. Institutions have no choice but to invest to develop and deliver innovative services whilst managing ever greater IT and cybersecurity risks. The pandemic and announcement of lockdown measures posed a significant challenge for banks’ technology teams as […]

Federal reserve board publishes 2020 stress testing results and additional sensitivity analysis
The Federal Reserve Board released stress test results for DFAST 2020 including additional sensitivity analysis, considering the COVID19 outbreak, to assess the resiliency of large banks under three hypothetical recessions, or downside scenarios, that could result from the coronavirus event. Furthermore, the Board provides guidance for large banks to maintain resiliency during economic uncertainties from […]

Are more stringent gender diversity measures required?
Gender equality, while not systematically embedded in national laws, is clearly set in European law. The Capital Requirements Regulation (CRR) requires financial institutions to adopt a policy promoting diversity within their management bodies and, for the most significant ones, to set targets to reach gender-balanced boards. Despite these regulatory requirements, the conclusions of the European […]

Key considerations on institutions’ credit IRB and IFRS 9 models
Mazars provides an update on recent developments affecting financial institutions’ credit capital and provision models with focus on the EBA IRB Roadmap and COVID-19 relief measures. Before the onset of the COVID-19 global pandemic, regulatory bodies across the Eurozone published guidance to financial institutions as part of the European Banking Authority’s (EBA) Basel III implementation […]

How will COVID-19 affect the financial regulatory response to climate change?
At first glance, regulatory authorities appear to have deprioritised the issue of climate change. However, a closer look would suggest otherwise and climate change in reality remains a key long-term priority of national and European regulators. In some areas, regulatory action on climate change has been delayed Central banks around the world have taken steps […]

Regulatory flexibility gives banks the tools to support the economy during the Covid-19 pandemic
With banks no longer the weak link in the financial system, they now have a key role to play in supporting the real economy to survive the crisis caused by the Covid-19 pandemic. The significant strengthening of prudential regulation over the past decade since the 2008 financial crisis has enabled banking institutions to post solid levels […]

Raising the bar
One of the key takeaways of integrated reporting is that non-financial information ultimately has an impact on a company’s value. It’s for this reason that insurance giant Generali – an international Group based in Italy – prefers to use the term pre-financial rather than non-financial information. For Massimo Romano, who leads Generali’s Group Integrated Reporting […]
